Cloud communications provider Twilio has revealed that unidentified threat actors took advantage of an unauthenticated endpoint in Authy to identify data associated with Authy accounts, including users' cell phone numbers. The company said it took steps to secure the endpoint to no longer accept unauthenticated requests. The development comes days after an online persona named ShinyHunters
...moreSummary
Total Articles Found: 23
Top sources:
Top Keywords:
Top Authors
Top Articles:
- Third-Party ChatGPT Plugins Could Lead to Account Takeovers
- Twitter Limits SMS-Based 2-Factor Authentication to Blue Subscribers Only
- FIRST Announces CVSS 4.0 - New Vulnerability Scoring System
- WordPress Security Alert: New Linux Malware Exploiting Over Two Dozen CMS Flaws
- SLAM Attack: New Spectre-based Vulnerability Impacts Intel, AMD, and Arm CPUs
- CISA Issues Urgent Warning: Adobe ColdFusion Vulnerability Exploited in the Wild
- Twilio's Authy App Breach Exposes Millions of Phone Numbers
- Google's Shift to Rust Programming Cuts Android Memory Vulnerabilities by 52%
- Over 4,500 WordPress Sites Hacked to Redirect Visitors to Sketchy Ad Pages
- Urgent WordPress Update Fixes Critical Flaw in Jetpack Plugin on Million of Sites
Twilio's Authy App Breach Exposes Millions of Phone Numbers

Published: 2024-07-04 03:37:00
Popularity: 152
Author: info@thehackernews.com (The Hacker News)
🤖: ""Hacked phonebook""
OVHcloud Hit with Record 840 Million PPS DDoS Attack Using MikroTik Routers

Published: 2024-07-05 12:20:00
Popularity: 91
Author: info@thehackernews.com (The Hacker News)
🤖: "DDoS disaster"
French cloud computing firm OVHcloud said it mitigated a record-breaking distributed denial-of-service (DDoS) attack in April 2024 that reached a packet rate of 840 million packets per second (Mpps). This is just above the previous record of 809 million Mpps reported by Akamai as targeting a large European bank in June 2020. The 840 Mpps DDoS attack is said to have been a combination of a TCP
...moreNew Malware Targets Exposed Docker APIs for Cryptocurrency Mining

Published: 2024-06-18 09:41:00
Popularity: 64
Author: info@thehackernews.com (The Hacker News)
🤖: ""docker hack""
Cybersecurity researchers have uncovered a new malware campaign that targets publicly exposed Docket API endpoints with the aim of delivering cryptocurrency miners and other payloads. Included among the tools deployed is a remote access tool that's capable of downloading and executing more malicious programs as well as a utility to propagate the malware via SSH, cloud analytics platform Datadog
...moreThird-Party ChatGPT Plugins Could Lead to Account Takeovers

Published: 2024-03-15 11:34:00
Popularity: 322
Author: info@thehackernews.com (The Hacker News)
Cybersecurity researchers have found that third-party plugins available for OpenAI ChatGPT could act as a new attack surface for threat actors looking to gain unauthorized access to sensitive data. According to new research published by Salt Labs, security flaws found directly in ChatGPT and within the ecosystem could allow attackers to install malicious plugins without users' consent
...moreWordPress Bricks Theme Under Active Attack: Critical Flaw Impacts 25,000+ Sites

Published: 2024-02-20 09:08:00
Popularity: 134
Author: info@thehackernews.com (The Hacker News)
A critical security flaw in the Bricks theme for WordPress is being actively exploited by threat actors to run arbitrary PHP code on susceptible installations. The flaw, tracked as CVE-2024-25600 (CVSS score: 9.8), enables unauthenticated attackers to achieve remote code execution. It impacts all versions of the Bricks up to and including 1.9.6. It has been addressed by the theme developers in&
...moreWarning: New Malware Emerges in Attacks Exploiting Ivanti VPN Vulnerabilities

Published: 2024-02-01 07:43:00
Popularity: 58
Author: info@thehackernews.com (The Hacker News)
Google-owned Mandiant said it identified new malware employed by a China-nexus espionage threat actor known as UNC5221 and other threat groups during post-exploitation activity targeting Ivanti Connect Secure VPN and Policy Secure devices. This includes custom web shells such as BUSHWALK, CHAINLINE, FRAMESTING, and a variant of LIGHTWIRE. "CHAINLINE is a Python web shell backdoor that is
...moreItalian Businesses Hit by Weaponized USBs Spreading Cryptojacking Malware

Published: 2024-01-31 11:00:00
Popularity: 67
Author: info@thehackernews.com (The Hacker News)
A financially motivated threat actor known as UNC4990 is leveraging weaponized USB devices as an initial infection vector to target organizations in Italy. Google-owned Mandiant said the attacks single out multiple industries, including health, transportation, construction, and logistics. "UNC4990 operations generally involve widespread USB infection followed by the deployment of the
...moreSLAM Attack: New Spectre-based Vulnerability Impacts Intel, AMD, and Arm CPUs

Published: 2023-12-09 11:52:00
Popularity: 188
Author: info@thehackernews.com (The Hacker News)
Researchers from the Vrije Universiteit Amsterdam have disclosed a new side-channel attack called SLAM that could be exploited to leak sensitive information from kernel memory on current and upcoming CPUs from Intel, AMD, and Arm. The attack is an end-to-end exploit for Spectre based on a new feature in Intel CPUs called Linear Address Masking (LAM) as well as its analogous
...moreFIRST Announces CVSS 4.0 - New Vulnerability Scoring System

Published: 2023-11-02 05:19:00
Popularity: 231
Author: info@thehackernews.com (The Hacker News)
The Forum of Incident Response and Security Teams (FIRST) has officially announced CVSS v4.0, the next generation of the Common Vulnerability Scoring System standard, more than eight years after the release of CVSS v3.0 in June 2015. "This latest version of CVSS 4.0 seeks to provide the highest fidelity of vulnerability assessment for both industry and the public," FIRST said in a statement.
...moreNew Critical Security Flaws Expose Exim Mail Servers to Remote Attacks

Published: 2023-09-30 04:14:00
Popularity: 78
Author: info@thehackernews.com (The Hacker News)
Multiple security vulnerabilities have been disclosed in the Exim mail transfer agent that, if successfully exploited, could result in information disclosure and remote code execution. The list of flaws, which were reported anonymously way back in June 2022, is as follows - CVE-2023-42114 (CVSS score: 3.7) - Exim NTLM Challenge Out-Of-Bounds Read Information Disclosure Vulnerability
...moreUrgent WordPress Update Fixes Critical Flaw in Jetpack Plugin on Million of Sites

Published: 2023-06-01 04:01:00
Popularity: 141
Author: info@thehackernews.com (The Hacker News)
WordPress has issued an automatic update to address a critical flaw in the Jetpack plugin that’s installed on over five million sites. The vulnerability, which was unearthed during an internal security audit, resides in an API present in the plugin since version 2.0, which was released in November 2012. “This vulnerability could be used by authors on a site to manipulate any files in the
...morePackagist Repository Hacked: Over a Dozen PHP Packages with 500 Million Installs Compromised

Published: 2023-05-05 09:52:00
Popularity: 87
Author: info@thehackernews.com (The Hacker News)
PHP software package repository Packagist revealed that an "attacker" gained access to four inactive accounts on the platform to hijack over a dozen packages with over 500 million installs to date. "The attacker forked each of the packages and replaced the package description in composer.json with their own message but did not otherwise make any malicious changes," Packagist's Nils Adermann said
...moreCISA Issues Urgent Warning: Adobe ColdFusion Vulnerability Exploited in the Wild

Published: 2023-03-16 04:47:00
Popularity: 155
Author: info@thehackernews.com (The Hacker News)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on March 15 added a security vulnerability impacting Adobe ColdFusion to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The critical flaw in question is CVE-2023-26360 (CVSS score: 8.6), which could be exploited by a threat actor to achieve arbitrary code execution. "Adobe ColdFusion
...moreTwitter Limits SMS-Based 2-Factor Authentication to Blue Subscribers Only

Published: 2023-02-18 11:10:00
Popularity: 292
Author: info@thehackernews.com (The Hacker News)
Twitter has announced that it's limiting the use of SMS-based two-factor authentication (2FA) to its Blue subscribers. "While historically a popular form of 2FA, unfortunately we have seen phone-number based 2FA be used – and abused – by bad actors," the company said. "We will no longer allow accounts to enroll in the text message/SMS method of 2FA unless they are Twitter Blue subscribers."
...moreResearchers Hijack Popular NPM Package with Millions of Downloads

Published: 2023-02-16 18:30:00
Popularity: 118
Author: info@thehackernews.com (The Hacker News)
A popular npm package with more than 3.5 million weekly downloads has been found vulnerable to an account takeover attack. "The package can be taken over by recovering an expired domain name for one of its maintainers and resetting the password," software supply chain security company Illustria said in a report. While npm's security protections limit users to have only one active email address
...moreOver 4,500 WordPress Sites Hacked to Redirect Visitors to Sketchy Ad Pages

Published: 2023-01-25 16:11:00
Popularity: 143
Author: info@thehackernews.com (The Hacker News)
A massive campaign has infected over 4,500 WordPress websites as part of a long-running operation that's been believed to be active since at least 2017. According to GoDaddy-owned Sucuri, the infections involve the injection of obfuscated JavaScript hosted on a malicious domain named "track[.]violetlovelines[.]com" that's designed to redirect visitors to undesirable sites. The latest operation
...moreWordPress Security Alert: New Linux Malware Exploiting Over Two Dozen CMS Flaws

Published: 2023-01-02 07:50:00
Popularity: 212
Author: info@thehackernews.com (The Hacker News)
WordPress sites are being targeted by a previously unknown strain of Linux malware that exploits flaws in over two dozen plugins and themes to compromise vulnerable systems. "If sites use outdated versions of such add-ons, lacking crucial fixes, the targeted web pages are injected with malicious JavaScripts," Russian security vendor Doctor Web said in a report published last week. "As a result,
...moreChinese Nationals Arrested for Laundering $73 Million in Pig Butchering Crypto Scam

Published: 2024-05-19 09:46:00
Popularity: 51
Author: info@thehackernews.com (The Hacker News)
The U.S. Department of Justice (DoJ) has charged two arrested Chinese nationals for allegedly orchestrating a pig butchering scam that laundered at least $73 million from victims through shell companies. The individuals, Daren Li, 41, and Yicheng Zhang, 38, were arrested in Atlanta and Los Angeles on April 12 and May 16, respectively. The foreign nationals have been "charged for leading a scheme
...moreMalicious Python Package Hides Sliver C2 Framework in Fake Requests Library Logo

Published: 2024-05-13 06:18:00
Popularity: 67
Author: info@thehackernews.com (The Hacker News)
Cybersecurity researchers have identified a malicious Python package that purports to be an offshoot of the popular requests library and has been found concealing a Golang-version of the Sliver command-and-control (C2) framework within a PNG image of the project's logo. The package employing this steganographic trickery is requests-darwin-lite, which has been
...moreBitcoin Forensic Analysis Uncovers Money Laundering Clusters and Criminal Proceeds
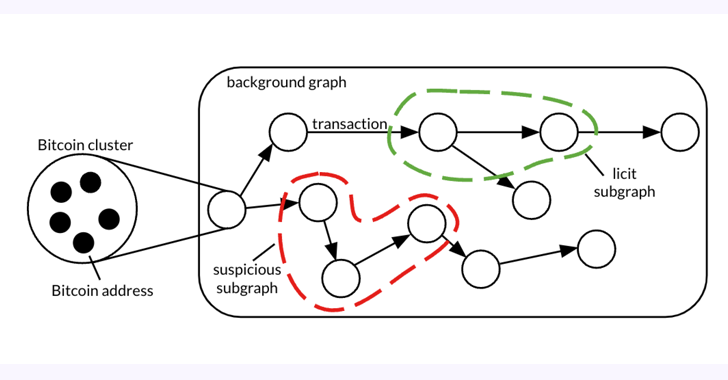
Published: 2024-05-01 14:25:00
Popularity: 88
Author: info@thehackernews.com (The Hacker News)
A forensic analysis of a graph dataset containing transactions on the Bitcoin blockchain has revealed clusters associated with illicit activity and money laundering, including detecting criminal proceeds sent to a crypto exchange and previously unknown wallets belonging to a Russian darknet market. The findings come from Elliptic in collaboration with researchers from the&
...moreCritical Flaws in Traccar GPS System Expose Users to Remote Attacks

Published: 2024-08-26 07:45:00
Popularity: 47
Author: info@thehackernews.com (The Hacker News)
🤖: ""System compromised""
Two security vulnerabilities have been disclosed in the open-source Traccar GPS tracking system that could be potentially exploited by unauthenticated attackers to achieve remote code execution under certain circumstances. Both the vulnerabilities are path traversal flaws and could be weaponized if guest registration is enabled, which is the default configuration for Traccar 5, Horizon3.ai
...moreGoogle's Shift to Rust Programming Cuts Android Memory Vulnerabilities by 52%

Published: 2024-09-25 17:00:00
Popularity: 146
Author: info@thehackernews.com (The Hacker News)
🤖: "Rust proof 💻"
Google has revealed that its transition to memory-safe languages such as Rust as part of its secure-by-design approach has led to the percentage of memory-safe vulnerabilities discovered in Android dropping from 76% to 24% over a period of six years. The tech giant said focusing on Safe Coding for new features not only reduces the overall security risk of a codebase, but also makes the switch
...more5 Most Common Malware Techniques in 2024

Published: 2024-11-07 09:48:00
Popularity: 47
Author: info@thehackernews.com (The Hacker News)
🤖: "Ransomware alert"
Tactics, techniques, and procedures (TTPs) form the foundation of modern defense strategies. Unlike indicators of compromise (IOCs), TTPs are more stable, making them a reliable way to identify specific cyber threats. Here are some of the most commonly used techniques, according to ANY.RUN's Q3 2024 report on malware trends, complete with real-world examples. Disabling of Windows Event Logging
...more